Next level IIoT Security
IIoT - Industrial Internet Of Things - is the dedicated IoT sector for industries. Because of the industry 4.0 revolution, everything is moving fast. Every day brings new products, new software, platforms and services. Most companies work hard to embrace the current digital era, some think of it, while the others are not aware or interested yet.
This kind of projects mobilizes a lot of resources, time and money. At the same time, the company Information System is getting more complicated and a lot of devices are becoming “smart” through internet accessibility. That provides a lot of tremendous advantages. But it also weakens the security of the company’s system by expanding the attack surface.
IIoT suffers from a lack of experience in cybersecurity
The Industrial IoT Market is highly competitive and features the presence of a large number of foreign and regional players. The market has witnessed growing rivalry between vendors based on the pricing model, differentiation of technology, brand name, service quality, product differentiation, and technical expertise. Source
Security is not a priority for IIoT device makers because of price competitivity, device complexity and the lack of experience in cybersecurity. For sure the price competitivity is a big factor.
Nowadays, there can be large gaps while dealing with cybersecurity. Indeed, while large companies invests in one or many cybersecurity teams, for small companies on the other hand, it’s another story. The complexity of securing an IIoT network is growing accordingly to the quantity of devices connected and data collected.
IIoT extra complexity
IT sector has been experiencing cyber threats for a long time, facing security breaches through various attack vectors and threats like virus, Botnet, Social Engineering, ransomware, phishing, DDoS, etc. And that’s still a very challenging job.
IIoT security imply a new level of complexity with the heterogenity of devices, constant network reconfiguration because of adding or removing devices, scaling, latency, privacy, OT (Operational Technologies) and IT (Information Technologies) network interconnectivity and lack of standards. And that’s even more challenging when you know that, for many IIoT projects the goal is to make automated smart decisions in real-time.
And because of the IIoT concept nature you have to also consider the following threats :
- Reverse Engineering
- DDos
- Man in the Middle
- Replay Attack
- Brute Force
- Buffer Overflow
- Botnet
- Ransomware
- Malicious Attack
- Resource Exhaustion
- SQL Injection
- Metadata Spoofing
- Hardware tampering
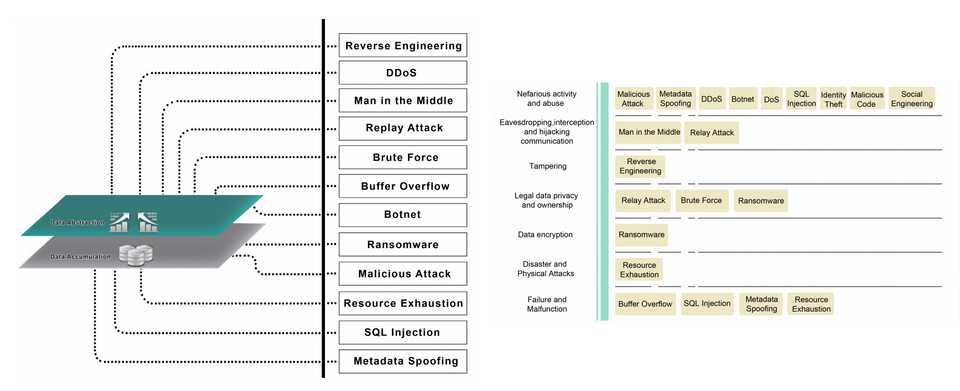 Source - Industrial IoT Security Threats and Conerns by Considering Cisco and Microsoft IoT references Models by Zeinab Bakhshi, Ali Balador and Jawad Mustafa
Source - Industrial IoT Security Threats and Conerns by Considering Cisco and Microsoft IoT references Models by Zeinab Bakhshi, Ali Balador and Jawad Mustafa
And those threats need to be addresses in an environement where we are struggling with the rise of botnets and ransomwares, outdated legacy security, infrequent security updates, user privacy, …
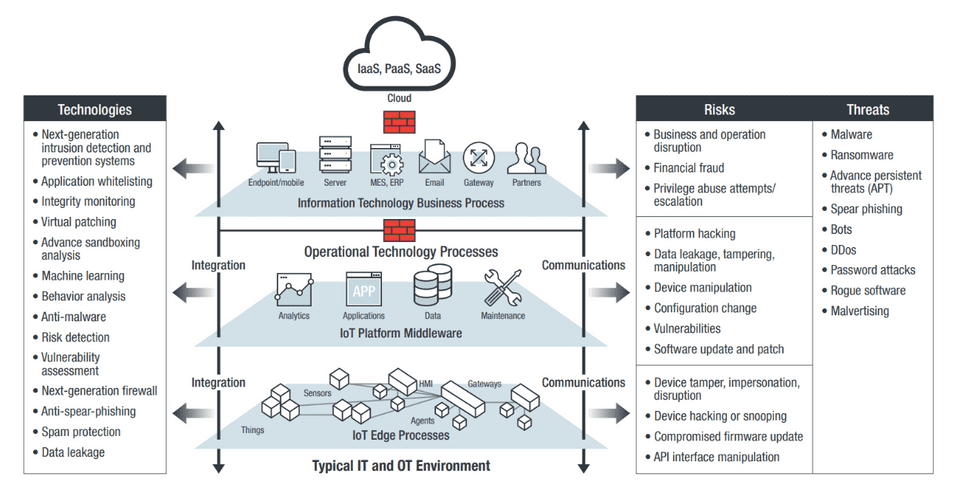 Source: Trend Micro
Source: Trend Micro
We have a notorious example of an OT system compromised through the IT network. The December 2015 cyberattack against a power grid in Ukraine allowed to infect and shutdown critical systems and disrupt power in many houses.
The complexity of Information System is growing fast, and if you add the IIoT complexity, it can become a nightmare. Industries and companies adopting the IIoT have to plan and operate like tech companies in order to manage both physical and digital components securely.
Is Machine Learning an option ?
Machine learning (ML) is an application of artificial intelligence (AI) that provides systems the ability to automatically learn and improve from experience without being explicitly programmed - Source Blog Expert System
Basically, machine learning is a bunch of computer algorithms which are getting better through experience. It can be trained with massive dataset to generate a constantly evolving model which can be use to predict outcomes.
NB: I do not like to use the “smart” word speaking of ML. Smart can usually be used for the people who created ML Algorithms.
This is used in a wide variety of applications :
- predictive maintenance,
- industrial vision or computer vision,
- Siri, Alexa or Google Assistant,
- Image recognition,
- …
The very interesting part of this technology is the capacity to adapt models in real-time depending of dataset and dynamic parameters. Theoretically speaking we can imagine training models for an IT + OT Security System.
The ML system would be able to detect both known and unknown attacks. About the known ones you can train models to predict attacks by learning attack patterns or events from examples. About the unknowns one, it can detect unusual event, series of events, behaviors, or patterns and alert accordingly.
With ML you can train models which can adapt security rules quickly depending of the changing environment: adding/removing devices, apps, cloud services, … in IT and OT systems.
You can read the JCSE (Journal of Computer Sciences and Engineering) paper about Machine Learning DDoS (Distributed Denial of service) Detection Using Stochastic Gradient Boosting. M Devendra Prasad, Prasanta Babu and C Amarnath improved the performance of their models to reach 100% detection by using a dataset of diversified DDoS flows with more than 10 million bidirectional flows and meticulously tuning the hyperparameters. Basically they gave more data to feed the beast and generate a more accurate detection model.
I think there are many flaws using ML for cybersecurity especially when the attacker knows that’s the company is using this kind of technology. Again Machine Learning is made of algorithms. You can beat an algorithm. But I find this approach very intersting for answering the complexity of IT & OT systems.
By the way, some of the technology leader companies already uses ML for security purposes like Google and Apple with facial recognition for authentication on your smartphones ;)
If you want to read some papers about IoT security and Machine Learning:
- IoT Security techniques Based on ML - https://arxiv.org/pdf/1801.06275.pdf
- Machine Learning in IoT Security Current Solutions and Future Challenges - https://arxiv.org/pdf/1904.05735.pdf
Solving IIoT Security Challenge
 We have seen that the security challenge is not just about IIoT. It’s all about IT and OT environments. There is a clear lack of knowledge about complex security and risk mitigiation by the OT staff.. On the other hands IT specialists are not familiar with OT environments.
We have seen that the security challenge is not just about IIoT. It’s all about IT and OT environments. There is a clear lack of knowledge about complex security and risk mitigiation by the OT staff.. On the other hands IT specialists are not familiar with OT environments.
IIoT is made of multiple constantly growing and evolving components. Each one can be the next security breach.
So we all need to step up and change/adapt our approaches.
Firstly, the device makers needs to adopt a secure-by-design methodology and stop adding bad security layers as an after thought. We have a lot of great cybersecurity experts outhere. Just contact them, they will be glad to help you.
Secondly, we need to train the communication between OT and IT teams. They need to identify the industrial assets and implement accordingly a risk, threat and security management process.
Finally, discover, find, adapt, use, the best tools, technologies and skills to help you in this process.
As a reminder, when industrial systems are hacked the effects can be catastrophic.

